1. Introduction to Windows Registry Forensics
The Windows Registry is a crucial source of forensic evidence. Windows Registry Forensics helps analysts uncover system activity, user behavior, and malware persistence. Moreover, this article introduces key artifacts, tools, and techniques for effective Registry analysis.
Forensic analysts uncovered file exfiltration evidence in a corporate espionage case by analyzing USB connection records in the SYSTEM hive, proving data theft.
This case highlights why the Windows Registry is one of the richest sources of forensic evidence. Specifically, the Windows Registry contains a wealth of system, user, and application-generated data that can reveal:
- Login history and authentication artifacts
- Recently accessed files and executed programs
- USB device connections and removable media usage
- Malware persistence mechanisms and system modifications
- Security configurations and audit settings
Forensic tools such as RegRipper, FTK Registry Viewer, and Registry Explorer can automate much of the extraction process. However, a deep technical understanding of Windows Registry Forensics is essential for validating tool outputs, manually extracting artifacts, and correlating registry data with other forensic evidence.
Consequently, this article provides a foundational introduction to Windows Registry forensics, covering registry structure, analysis methods, and forensic extraction techniques.
2. Structure of the Windows Registry
The Windows Registry is structured into hives, each containing important forensic artifacts that can reveal user activity, system configurations, and potential security risks. Therefore, understanding these hives is critical for reconstructing user activity and investigating security incidents.
At the highest level, the registry is organized into root keys, which serve as logical groupings for system and user settings. The two most relevant for forensic analysis are:
- HKEY_LOCAL_MACHINE (HKLM) — Stores system-wide settings that apply to all users on the machine, including configuration for hardware, security, installed applications, and drivers.
- HKEY_CURRENT_USER (HKCU) — Stores user-specific settings, including recently accessed files, executed programs, and desktop preferences.
Each of these root keys contains registry hives, which store the actual forensic artifacts that analysts examine. Below is a breakdown of the most relevant hives for registry investigations:
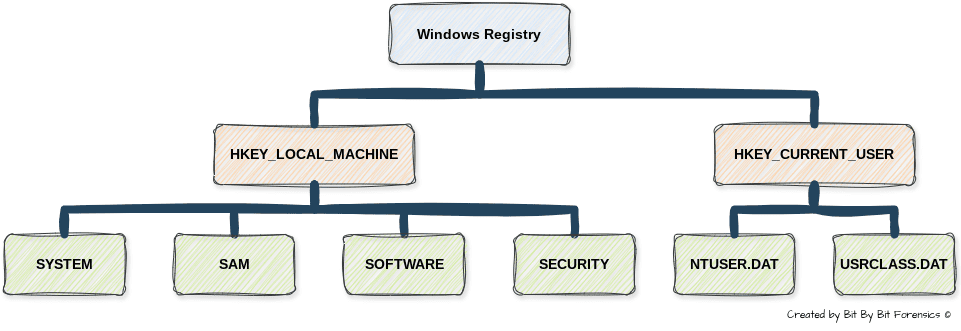
2.1 SYSTEM Hive
Stores system-wide configuration settings, including hardware information, network setup, and connected devices.
C:\Windows\System32\config\SYSTEM
Forensic Value: Helps analysts track when USB devices were connected, identify boot configurations, and investigate time zone settings that impact forensic timestamps.
2.2 SAM (Security Accounts Manager) Hive
Contains user account data, including usernames, group memberships, and password hashes (NTLM hashes).
C:\Windows\System32\config\SAM
Forensic Value: Useful for identifying local user accounts, determining last logon timestamps, and extracting credentials for password analysis.
2.3 SOFTWARE Hive
Tracks installed applications, Windows settings, and system-wide configurations.
C:\Windows\System32\config\SOFTWARE
Forensic Value: Reveals installed and uninstalled programs, application usage history, persistence mechanisms (e.g., auto-start entries), and even malware implants.
2.4 SECURITY Hive
Stores local security policies, group policy settings, and authentication configurations.
C:\Windows\System32\config\SECURITY
Forensic Value: Helps analysts determine audit policies, encryption settings, and access control configurations, which are critical for security investigations and policy enforcement.
2.5 NTUSER.DAT Hive
Captures user activity such as recently accessed files, executed programs, and desktop customizations.
C:\Users\<USERNAME>\NTUSER.DAT
Forensic Value: A goldmine for reconstructing user interactions with the system, including program execution history, opened documents, and user preferences.
2.6 USRCLASS.DAT Hive
Stores additional user-specific settings, particularly related to modern Windows apps and shell extensions.
C:\Users\<USERNAME>\AppData\Local\Microsoft\Windows\UsrClass.dat
Forensic Value: Often overlooked, but can contain Jump List artifacts, shell interactions, and application-specific settings that provide insight into how a user interacted with the Windows environment.
3. Live vs. Offline Registry Analysis
Windows Registry forensics analysis can be performed on a live system or from an offline forensic image.
3.1 Live Registry Analysis
Live analysis allows forensic analysts to interact with an active system’s registry, but it comes with risks of system modifications and volatile data loss.
Methods of Live Analysis:
- Regedit.exe — The built-in Windows Registry Editor.
- Reg Query (CLI tool) — Used to extract registry keys via command line.
- PowerShell Cmdlets (
Get-ItemProperty) – Retrieves registry values programmatically.
Advantages:
- Real-time access to registry data.
- Can detect dynamic malware behavior.
Disadvantages:
- Risk of altering forensic evidence.
- Malware can alter live registry artifacts, including LastWrite timestamps, to obscure its activity. To uncover anomalies, forensic analysts must cross-reference event logs and NTFS timestamps.
3.2 Offline Registry Analysis
Offline Windows Registry forensics analysis is the preferred forensic method as it prevents modifications and ensures data integrity.
Methods of Offline Analysis:
- Extract registry hives from forensic disk images.
- Use tools like FTK Imager to acquire SYSTEM, SAM, SOFTWARE, SECURITY, and NTUSER.DAT files.
- Analyze registry artifacts using Registry Explorer, RegRipper, or Autopsy.
Advantages:
- Prevents contamination of forensic evidence.
- Allows for historical registry recovery via volume shadow copies.
Disadvantages:
- Does not capture volatile registry artifacts (e.g., memory-resident malware).
4. How Windows Updates & System Changes Impact Registry Artifacts
Windows system updates, software installations, and user modifications constantly alter registry data. Forensic analysts should be aware of:
4.1 Deleted & Overwritten Registry Keys
- When a key is deleted, remnants may persist in unallocated registry space or Volume Shadow Copies.
- Tools like Registry Explorer can recover deleted registry entries.
4.2 Transactional Registry Operations
- Windows writes registry changes in transactions, which can create artifacts even if a key is later modified or removed. For instance, forensic analysts have recovered remnants of deleted malware persistence keys using Volume Shadow Copies, helping attribute system modifications to a specific user session.
- Windows Transaction Logs (TxR logs) are typically stored in
C:\Windows\System32\config\TxR. These logs may preserve registry remnants even after deletion, making them valuable for forensic analysis.
4.3 System Restore Points & Volume Shadow Copies
- Previous versions of registry hives may be recovered from:
C:\Windows\System32\config\RegBack(Disabled by default in Windows 10 Version 1803+). - Volume Shadow Copies (VSCs) store historical snapshots of the registry, allowing forensic analysts to recover deleted or modified keys, compare registry states over time, and reconstruct user activity before system changes occurred. They are crucial for tracking malware persistence, recovering lost configurations, and validating timestamps against event logs.
5. Registry Extraction Methods
5.1 Manual Extraction from Disk Images
Forensic analysts can manually extract registry hives from an acquired disk image.
To manually extract the SAM registry hive from a Volume Shadow Copy, use the following command:
copy \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM C:\Forensics\SAM
To manually extract the NTUSER.DAT registry hive for a specific user, use the following command:
copy C:\Users\JohnDoe\NTUSER.DAT C:\Forensics\NTUSER.DAT
5.2 Using Forensic Tools for Extraction
Forensic analysts use specialized tools to extract registry hives and analyze their contents for investigative insights. These tools allow analysts to recover deleted entries, parse key values, and correlate registry artifacts with other forensic evidence. Below is a breakdown of commonly used forensic tools and their functions:
- FTK Imager — Acquires raw registry hives from forensic disk images, live systems, or volume shadow copies. It preserves data integrity by creating a forensic image of the registry files, ensuring they can be examined without altering the original system.
- RegRipper — A command-line tool that parses registry keys and extracts forensic artifacts into a readable format. It automates the process of pulling valuable registry data, such as USB device history, user activity, and malware persistence mechanisms, by running specialized plugins tailored for forensic analysis.
- Registry Explorer — Provides a graphical interface for deep registry analysis, allowing analysts to navigate registry structures, recover deleted keys, and view LastWrite timestamps. It enables investigators to manually inspect registry artifacts, correlate timestamps, and identify suspicious modifications.
By leveraging these tools, forensic analysts can extract, parse, and interpret registry data to uncover user activity, system modifications, and potential security incidents.
6. Conclusion & Next Steps
Key Takeaways:
- The Windows Registry is a critical forensic artifact for tracking user and system activity.
- Understanding registry structure (SYSTEM, SAM, SOFTWARE, SECURITY, NTUSER.DAT) is essential for forensic analysis.
- Offline analysis is preferred over live registry examination for preserving evidence.
- Windows updates and anti-forensic techniques can impact registry artifacts, requiring advanced timeline reconstruction techniques.
What’s Next?
The next article in this series, “User Activity in the Windows Registry,” will cover:
- Tracking login sessions & authentication history
- Recent file access & executed programs
- USB device connection history
- Jump Lists and forensic correlation with event logs
While automated tools can expedite analysis, forensic analysts must understand the registry at a granular level to detect anomalies, validate tool output, and uncover artifacts that may evade detection.
🔍 In the next article, we’ll uncover how forensic analysts can track login sessions, executed programs, and USB activity through registry artifacts. Mastering these techniques is crucial for reconstructing forensic timelines and tracking user activity. Stay tuned as we dive deeper into registry artifacts in the next article!
14 thoughts on “Introduction to Windows Registry Forensics”